Goals of cyber security
Goals of cyber security
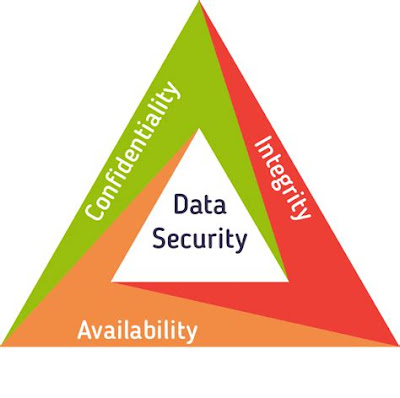
With lots of information being generated by an organization today, as we know the world is going digital, every piece of information is more or less stored in a software and as a user we must ensure our data is been stored in a secured website and as an organization it's their responsibility to keep the data confidential, maintain integrity and available as an when required. Most commonly termed as a CIA triad.
Three most important goals of cyber security are as follows :
Confidentiality -
The principle of confidentiality ensures that only the sender and the recipient(s) should be able to access the contents of a message. Confidentiality gets compromised if an unauthorized person gets an access to a message.
E.g
User A wants to send message to user B, another user C gets access to this message which is not desired and thus defeats the purpose of confidentiality. let's say A sends a confidential email to B which is accessed by C without the consent of A and B. This type of attack is called as interception
Interception causes loss of message confidentiality.
Integrity -
Data integrity ensures that the information is real, accurate and safe from any unauthorized user. Only an authorized entity has right to change, modify, edit the contents of data. If the contents of data are changed after the sender sends it, but before it reaches the intended recipient, we say the integrity of the data is lost.
E.g
Suppose you pay $100 for some goods to be purchased online, when you check your account statement it says $1000 used for that goods, this is the case of loss of message integrity.
User C tampers data originally sent by user A, which is actually destined for user B. User C somehow manages to access it, changes its contents and sends the changed message to user B. User B has no idea that the message is actually coming from user C and not A. This type of attack is known as modification.
Availability -
The principle of availability ensures that the data should remain available on time on demand for a user. for e.g due to intentional actions of another unauthorized user C, an authorized user A may not be able to contact a server computer B, this would defeat a principle of availability. This type of attack is known as interruption.
Interruption puts the availability of resources in danger





Comments
Post a Comment