MITM Attack
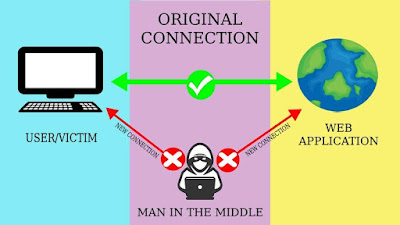
MITM Attack In this post you are going to learn, what is MITM attack, examples, phases, preventions & tools to perform MITM Attack. What is MITM Attack - A man-in-the-middle or person-in-the-middle (PITM) is a type of cyberattack where an attacker places himself between two users or computers and tries to intercept the data or alters the data or steals the data and forwards it to the sender/receiver. One more form of MITM is MITB i.e. man-in-the-browser where in, an attacker places a bot in the browser to steal the details of the users and then sends it to an attacker. Example - There are two users - A, B & there is an attacker in between them. User A asks user B to send public key of user B so that user A can encrypt the message and send it to the user B. User B sends it's public key to user A, since an attacker is in between them he gets the public key of user B and sends it's own public key to the user A. User A thinks the public key he received is of user B so he ...